9.8.Memory Mapping
\(9.8.\)Memory Mapping
Linux initializes the contents of a virtual memory area by associating it with an object on disk. Areas can be mapped to one of two types of objects:
Regular file in the Linux file system: The file section is divided into page-size pieces, with each piece containing the initial contents of a virtual page.
Anonymous file: The first time the CPU touches a virtual page in such an area, the kernel:
finds an appropriate victim page in physical memory,
swaps out the victim page if it is dirty, overwrites the victim page with binary zeros,
updates the page table to mark the page as resident.
- Once a virtual page is initialized, it is swapped back and forth between a special swap file maintained by the kernel. It's known as the swap space.
1.Sharred Objects Revisited
An object can be mapped into an area of virtual memory as either a shared object or a private object.
If a process maps a shared object into an area of its virtual address space, then any writes that the process makes to that area are visible to any other processes that have also mapped the shared object into their virtual memory. Further, the changes are also reflected in the original object on disk.
Changes made to an area mapped to a private object are not visible to other processes, and any writes that the process makes to the area are not reflected back to the object on disk.
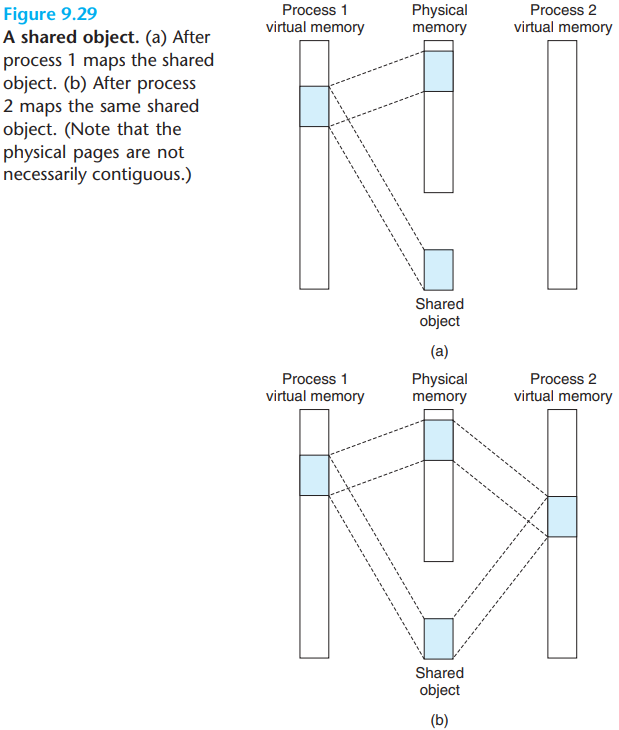
The kernel can quickly determine that process 1 has already mapped this object and can point the page table entries in process 2 to the appropriate physical pages.
The key point is that only a single copy of the shared object needs to be stored in physical memory.
Private objects are mapped into virtual memory using a technique known as copy-on-write:
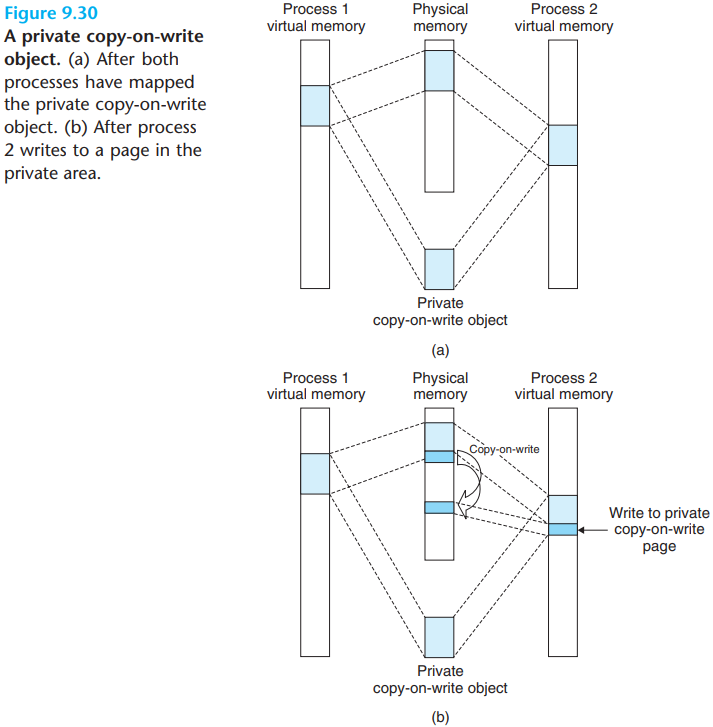
Two processes have mapped a private object into different areas of their virtual memories but share the same physical copy of the object.
For each process that maps the private object, the page table entries for the corresponding private area are flagged as read-only, and the area struct is flagged as private copy-on-write.
As soon as a process attempts to write to some page in the private area, the write triggers a protection fault:
The fault handler creates a new copy of the page in physical memory, updates the page table entry to point to the new copy, and then restores write permissions to the page.
When the fault handler returns, the CPU re-executes the write, which now proceeds normally on the newly created page.
2.The execve
Function Revisited
Suppose that we make the following call:
1 | execve("a.out", NULL, NULL); |
Delete existing user areas
Map private areas: Create new area structs for the code, data, bss, and stack areas of the new program:
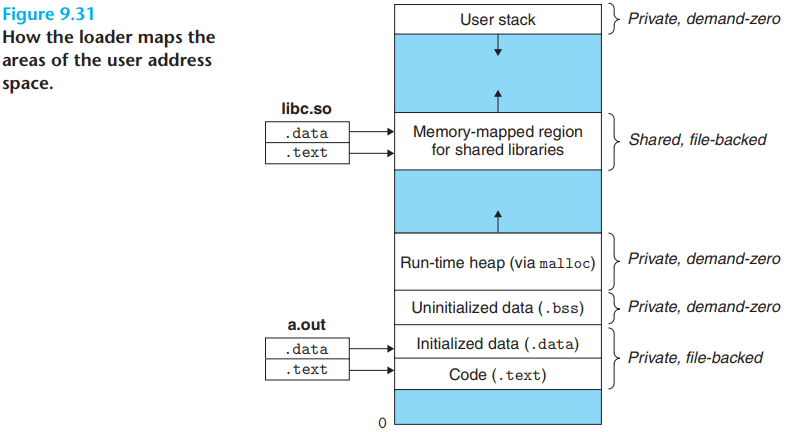
Map shared areas: If the
a.outprogram was linked with shared objects, then these objects are dynamically linked into the program, and then mapped into the shared region of the user’s virtual address space.Set the PC. The last thing is to set the program counter in the current process's context to point to the entry point in the code area.
3.User-Level
Memory Mapping with the mmap Function
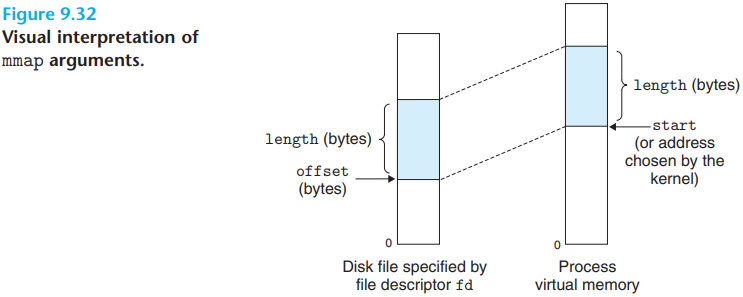
mmap function is used to create new areas of virtual
memory and to map objects into these areas:
1 |
|
The munmap function is used to delete regions of
virtual memory:
1 |
|
The munmap function deletes the area starting at virtual address
start and consisting of the next length
bytes.