9.5.Memory Protection
\(9.5.\)Memory Protection
A user process shouldn't be allowed to modify any virtual pages that are shared with other processes, unless all parties explicitly allow it(via calls to explicit interprocess communication system calls).
It is straightforward to control access to the contents of a virtual page by adding some additional permission bits to the PTE.
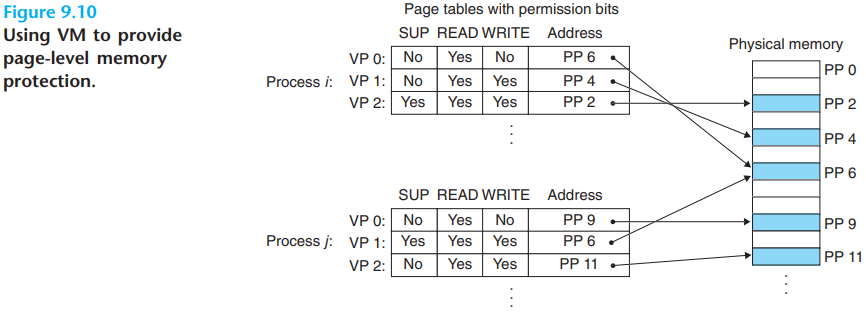
The
SUPbit indicates whether processes must be running in kernel(supervisor) mode to access the page.The
READandWRITEbits control read and write access to the page.If an instruction violates these permissions, then the CPU triggers a general protection fault that transfers control to an exception handler in the kernel, which sends a
SIGSEGVsignal to the offending process. Linux shells typically report this exception as a "segmentation fault".